Reverse Proxy Vs Proxy
Forward ProxyReverse ProxyProcesses Outgoing RequestsProcesses Incoming RequestsA Forward Proxy is just called a Proxy. When Someone says a proxy, that just means a forward proxy. An example of a forward proxy would be, for example if you work at a big firm, where there are a lot of computers/employees making a request to the same website to go get some information, (an example could be a LDAP server where the backed end service to it gets called most frequently), so this company may setup a forward proxy, so all the employees may send request to this forward proxy, which can do a bunch of things before it forwards the request to the server or a reverse proxy if it has one setup.Even though the server instances endpoints keep changing, the client endpoints remain same. Reverse proxy handles the incoming requests and delegates it to the server instances, even though the server instances scales up or down or if any server node instances fail.The reverse proxy handles a stable endpoint at the start (before it receives a incoming request), so the client endpoint does not change.The reverse proxy hides or shield’s the server instances from incoming traffic.How does the reverse proxy decide to which server instance to route?A forward proxy can do Content Filtering. May be a administrator at the company has setup up a forward proxy to stop certain malicious, censored, gambling or translation website traffic from coming in to the internal servers or to the internet traffic (external) from going out. A forward proxy acts as the first shield of defence.Reverse Proxy can be used as Load Balancers. There are 2 types of Load Balancers Level 4 & Level 7.Level 4 Load Balancers can handle UDP/TCP traffic.
It’s level 4 because of OSI networking model. They handle traffic by tapping at level 4 of OSI networking model.Level 7 Load Balancers handle HTTP/HTTPS incoming traffic. It’s Level 7 because it is level 7 in the OSI networking model, which is the Application layer. It can look at URI’s, HTTP Headers. The HTTP Headers can also direct which server instance to direct to.Also, with Reverse Proxy as a Load Balancer, you can do Server selection, A/B Testing, meaning you can dictate the reverse proxy configuration to direct the traffic based on the amount of incoming traffic load. Example, you can configure it to go to server instance 1 if the incoming traffic is 10% and go to server instance 2 if the incoming traffic is.
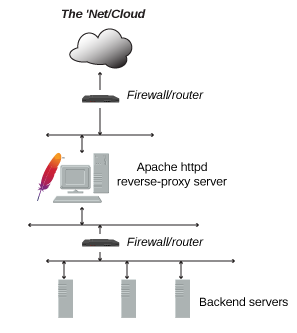
Forward ProxyA forward proxy is an intermediate server that sits between the client and the origin server. In order to get content from the web server, the client sends a request to the proxy server naming the web server as the target. The proxy then requests the content from the web server and returns it to the client. The client must be specially configured to use the forward proxy to access other sites.A typical usage of a forward proxy is to provide Internet access to internal clients that are otherwise restricted by a firewall or to explicitly block certain websites. The forward proxy can also use caching to reduce network usage for frequently accessed resources.To explain the forward proxy further, using the following setup:.
X = User computer on the company network. Y = The company proxy server e.g. Proxy.mycompany.com. Z = Web site that the user wants to visit, e.g.

Www.thebestwebsiteonthewholeinternet.comTypically, X would connect directly to the website Z (i.e. Once a forward proxy is configured, X would have to go through Y to access the website Z (i.e. X–Y–Z)Reverse ProxyA reverse proxy (or gateway), by contrast, appears to the client just like an ordinary web server. No special configuration on the client is necessary. The client makes ordinary requests for content in the namespace of the reverse proxy.
Web Proxy Vs Reverse Proxy
The reverse proxy then decides where to send those requests and returns the content as if it were itself the origin.A typical usage of a reverse proxy is to provide Internet users access to a server that is behind a firewall. Reverse proxies can also be used to balance load among several back-end servers or to provide caching for a slower back-end server.
Reverse Proxy Vs Forward Proxy
In addition, reverse proxies can be used simply to bring several servers into the same URL space.To explain the reverse proxy further, using the following setup:. X = User computer on the Internet. Y = The company proxy server e.g. Proxy.mycompany.com. Z = Web site that the user wants to visit that is hosted by the company, e.g.
Www.thebestwebsiteonthewholeinternet.comTypically, X would connect directly to the website Z (i.e. However, there may be reasons to prevent direct access to Z. Once a reverse proxy is configured, X would have to go through Y to access the website Z (i.e.
Unlike a forward proxy configuration, the user X does not know he is accessing the website on a server Z, because the user X only sees he is communicating with a server Y. The server Z is invisible to clients and only the proxy server Y is visible externally. Furthermore, a reverse proxy requires no explicit proxy configuration on the user computer side. The user computer X thinks it is only communicating with Y (i.e.
What Is A Reverse Proxy
X – Y), but the reality is that Y is sending all communication to Z. (i.e. X–Y–Z).Source/Further Reading:Posts navigation.